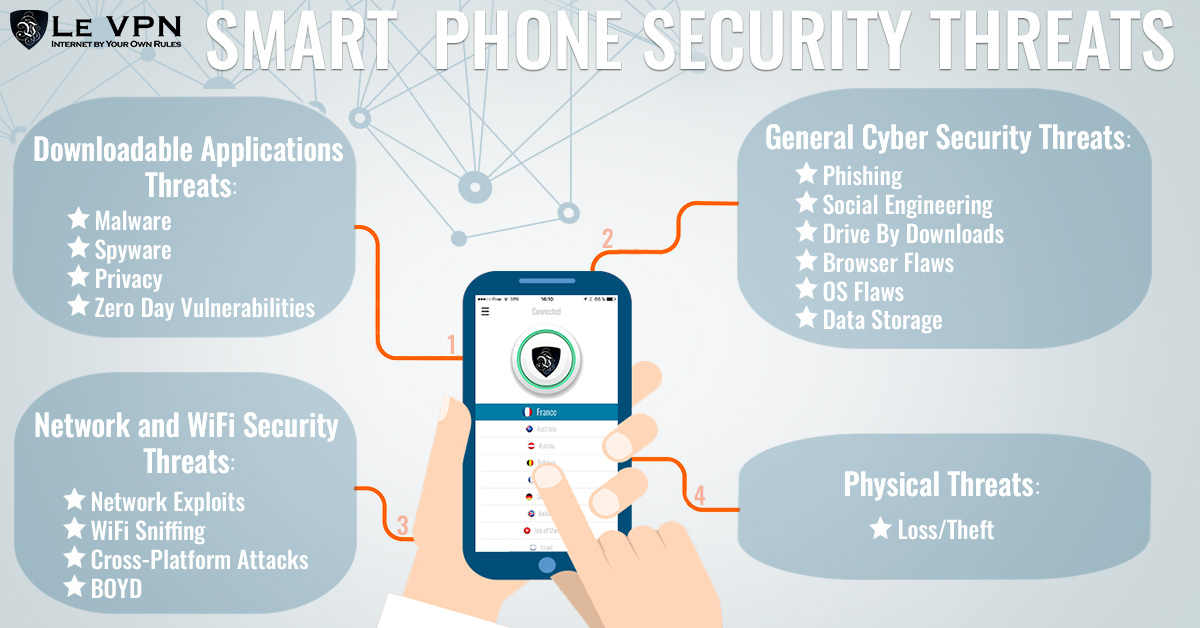
So, you’ve got your hands on the latest and greatest smartphone, but have you ever wondered what goes on behind the scenes? That sleek device in your pocket holds a world of secrets waiting to be unlocked. In this article, we will take you on a journey to master the art of in-depth phone analysis. From understanding the inner workings of your phone to uncovering hidden features and optimizing its performance, get ready to dive into the fascinating world that lies within your pocket companion. It’s time to become an expert in deciphering the mysteries of your phone!

Overview
In today’s digital age, where smartphones have become an integral part of our lives, understanding the importance of in-depth phone analysis is crucial. Whether you are an investigator, a forensic analyst, or someone who wants to protect their personal information, mastering the techniques of phone analysis can provide invaluable insights. In this comprehensive guide, we will delve into the benefits of mastering in-depth phone analysis and explore the various techniques, tools, and considerations involved in this field.
Understanding the Importance of In-Depth Phone Analysis
Phone analysis goes beyond just superficially examining a device; it involves a thorough exploration of the data stored within it. By conducting a detailed analysis, you can uncover vital information that may be critical in solving crimes, resolving disputes, or understanding someone’s behavior. Phone analysis is also essential for personal security, as it helps in identifying potential threats, protecting sensitive information, and ensuring the integrity of your device. In an era where communication primarily takes place through smartphones, in-depth phone analysis plays a pivotal role in investigations, forensics, and everyday life.
Benefits of Mastering In-Depth Phone Analysis
By mastering in-depth phone analysis, you gain access to a plethora of benefits that can aid in various scenarios. Firstly, it equips you with the tools to extract and recover deleted data, providing a second chance to access critical information that may have been intentionally or accidentally erased. Additionally, in-depth phone analysis allows you to analyze call logs, messages, internet and app usage, GPS and location data, and even social media presence. These insights can be instrumental in uncovering hidden patterns, establishing timelines, and verifying alibis. Moreover, comprehensive knowledge of mobile operating systems, hardware components, data recovery techniques, encryption, and security measures empowers individuals to protect their privacy, secure their devices, and counteract potential threats effectively.
Preparation for Phone Analysis
Before diving into the world of phone analysis, it is essential to make adequate preparations. Gathering the necessary tools and resources, such as cables, adapters, software applications, and forensic kits, ensures that you have all the right equipment at your disposal. Creating a proper workstation that is clean, well-lit, and adequately equipped with necessary devices and software is crucial for effective analysis. Moreover, obtaining proper permission or legal authorization is of utmost importance to maintain ethical standards and comply with applicable laws and regulations. Always ensure that you have obtained the necessary consents and permissions before conducting any phone analysis.
Phone Analysis Techniques
Initial Examination of the Phone
The initial examination of the phone involves inspecting the device for any signs of tampering or physical damage. It is essential to document the state of the phone, noting any visible markings, scratches, or abnormalities. This examination establishes the baseline for further analysis and helps detect any potential evidence or anomalies.
Data Extraction Methods
Data extraction is a critical step in phone analysis as it allows access to the device’s stored information. Various methods can be used for data extraction, such as logical extraction, physical extraction, cloud-based extraction, and backup analysis. Each method has its advantages and limitations, and selecting the appropriate technique depends on the specific requirements and the type of data being sought.
Analyzing Call Logs and Messages
Analyzing call logs and messages can provide valuable insights into the communication patterns, contacts, and timelines of the phone’s user. This information can be vital in establishing connections, verifying statements, and identifying potential leads. Through careful examination and correlation of call records and messages, patterns can emerge that may assist in understanding the context and motive behind certain activities.
Examining Internet and App Usage
With smartphones being used for internet browsing and app usage, examining these aspects can yield crucial information. Analyzing internet history, bookmarks, app usage logs, and stored credentials can provide insights into the user’s interests, activities, and online presence. Furthermore, it can help in identifying potential sources of evidence or identifying patterns that may be relevant to the investigation or analysis.
Recovering Deleted Files
The ability to recover deleted files is a powerful tool in phone analysis. Deleted files may still reside in the device’s memory or storage, waiting to be discovered. By utilizing specialized forensic software and techniques, it is often possible to recover deleted images, videos, documents, or other files that may be relevant to the investigation. Care must be taken during the recovery process to ensure the integrity of the evidence and compliance with legal requirements.
Analyzing GPS and Location Data
The analysis of GPS and location data can provide valuable insights into the movements, patterns, and whereabouts of the phone’s user. Location information collected by the device can be used to establish timelines, determine associations, or even reconstruct events. By analyzing GPS coordinates, geotags on photos, or location data from apps, investigators can gain a deeper understanding of the activities and movements of the phone’s user.
Exploring Social Media Presence
The prevalence of social media in today’s society makes it an important area of investigation in phone analysis. Examining social media presence can uncover connections, relationships, interests, and even potential motives. By analyzing social media accounts, messages, posts, and interactions, it is possible to gather valuable evidence or corroborate existing information. Care must be taken to follow legal guidelines and obtain proper authorization before accessing and analyzing social media data.
Understanding Mobile Operating Systems
To effectively analyze phones, it is crucial to have a comprehensive understanding of the various mobile operating systems. The major operating systems in use today include Android, iOS, Windows Phone, and Blackberry. Each operating system has its own unique characteristics, file structures, and security features, which must be taken into account during the analysis process. Familiarizing yourself with the intricacies of each mobile operating system enables effective investigation, data recovery, and analysis.
Analyzing Phone Hardware and Components
Understanding the hardware components of a phone is essential in analyzing device-specific characteristics and capabilities. Identifying different phone models and variants enables investigators to tailor their analysis techniques accordingly. Moreover, comprehending phone hardware specifications, such as processing power, memory capacity, and connectivity options, aids in assessing the phone’s capabilities and potential data storage limitations. Examining battery and power usage can also provide insights into usage patterns and battery life expectancy. Additionally, analyzing SIM cards and their associated data can be crucial in connecting phone usage to specific individuals or accounts. Furthermore, understanding phone sensors and the data they capture can provide cellular tower information, accelerometer data, or even biometric measurements.
Data Recovery and Forensics
Recovering deleted data is a critical aspect of phone analysis, as crucial evidence may have been deliberately or unintentionally erased. Specialized techniques, such as file carving, enable analysts to recover and reconstruct deleted files from the device’s storage. File carving involves identifying patterns in the storage space and restoring fragments of deleted files that may still exist. Additionally, forensic tools specifically designed for data recovery can aid in retrieving deleted information. Care must be taken during the recovery process to ensure the integrity of the data and avoid contamination or manipulation.

Understanding Encryption and Security Measures
As the security landscape evolves, encryption plays a vital role in safeguarding data on mobile devices. Understanding the various encryption methods employed on mobile devices allows analysts to assess the level of security and devise appropriate strategies and techniques for analysis. Breaking encryptions and passwords, while challenging, can be crucial in accessing encrypted data when authorized to do so. Analyzing security measures and countermeasures enables analysts to identify vulnerabilities, assess risks, and recommend appropriate security practices.
Analyzing Communication Apps
Communication apps have become an integral part of our daily lives, and analyzing their data can provide valuable insights. Investigating messaging apps, such as WhatsApp or Messenger, can uncover conversations, contacts, and potentially incriminating information. Analyzing voice and video communication apps, such as Skype or Facetime, allows analysts to piece together conversations, timestamps, and participant details. Examining email and file sharing apps, such as Gmail or Dropbox, enables the identification of attachments, shared files, and communication histories. The analysis of communication apps provides a wealth of information that can support investigations, dispute resolution, or personal security measures.

Documenting and Reporting Findings
Documenting and reporting findings is an integral part of any phone analysis process. Creating detailed reports and logs ensures that the analysis is transparent, well-documented, and reproducible if required. Reports should include a comprehensive overview of the analysis objectives, methodologies employed, key findings, and any supporting evidence. It is crucial to present findings in a clear and concise manner, using visual aids and graphics if necessary to enhance understanding. Additionally, maintaining the integrity of evidence throughout the analysis and reporting process is important to ensure the credibility and admissibility of the findings in legal proceedings.
Legal Considerations
Conducting phone analysis involves legal considerations to ensure compliance with privacy and data protection laws. Understanding the legal framework for phone analysis is important to ensure that investigators or analysts do not infringe upon individuals’ rights to privacy. Knowledge of relevant legislation, such as the General Data Protection Regulation (GDPR) or local privacy laws, is essential in conducting lawful phone analysis. Obtaining proper consent or legal authorization, adhering to chain of custody protocols, and protecting the confidentiality of personal information are key aspects of maintaining ethical and legal compliance in phone analysis.
In conclusion, in-depth phone analysis is a valuable skill that has significant implications in various domains. By mastering the techniques, understanding mobile operating systems, hardware components, data recovery methods, encryption, and security measures, individuals can unlock crucial evidence, protect their privacy, and enhance overall security. By following proper procedures, maintaining ethical standards, and complying with legal considerations, analysts can ensure that phone analysis is conducted in a responsible and lawful manner. In a world where smartphones hold a wealth of information, mastering the art of in-depth phone analysis is an invaluable skill that empowers individuals in both personal and professional pursuits.